Continuous Control Monitoring
JupiterOne's Continuous Control Monitoring (CCM) provides enterprise teams with automated, graph-powered validation of security control effectiveness across your entire technology ecosystem.
Designed for organizations with existing governance frameworks and dedicated compliance programs, CCM helps Platform Engineering, DevOps, and Security Architecture teams continuously validate that controls defined in your governance systems are working as intended in your actual infrastructure.
Overview
Continuous Control Monitoring enables your team to:
- Automate control validation using JupiterOne's graph-powered query engine to continuously test control effectiveness
- Monitor control status in real-time across all your integrated cloud platforms, security tools, and IT infrastructure
- Map controls to multiple frameworks including CIS benchmarks for AWS, Azure, GCP, and other standards
- Detect configuration drift automatically as your infrastructure changes
- Visualize control health through dashboards showing compliance status and control test results
- Bridge the gap between governance requirements and actual infrastructure reality
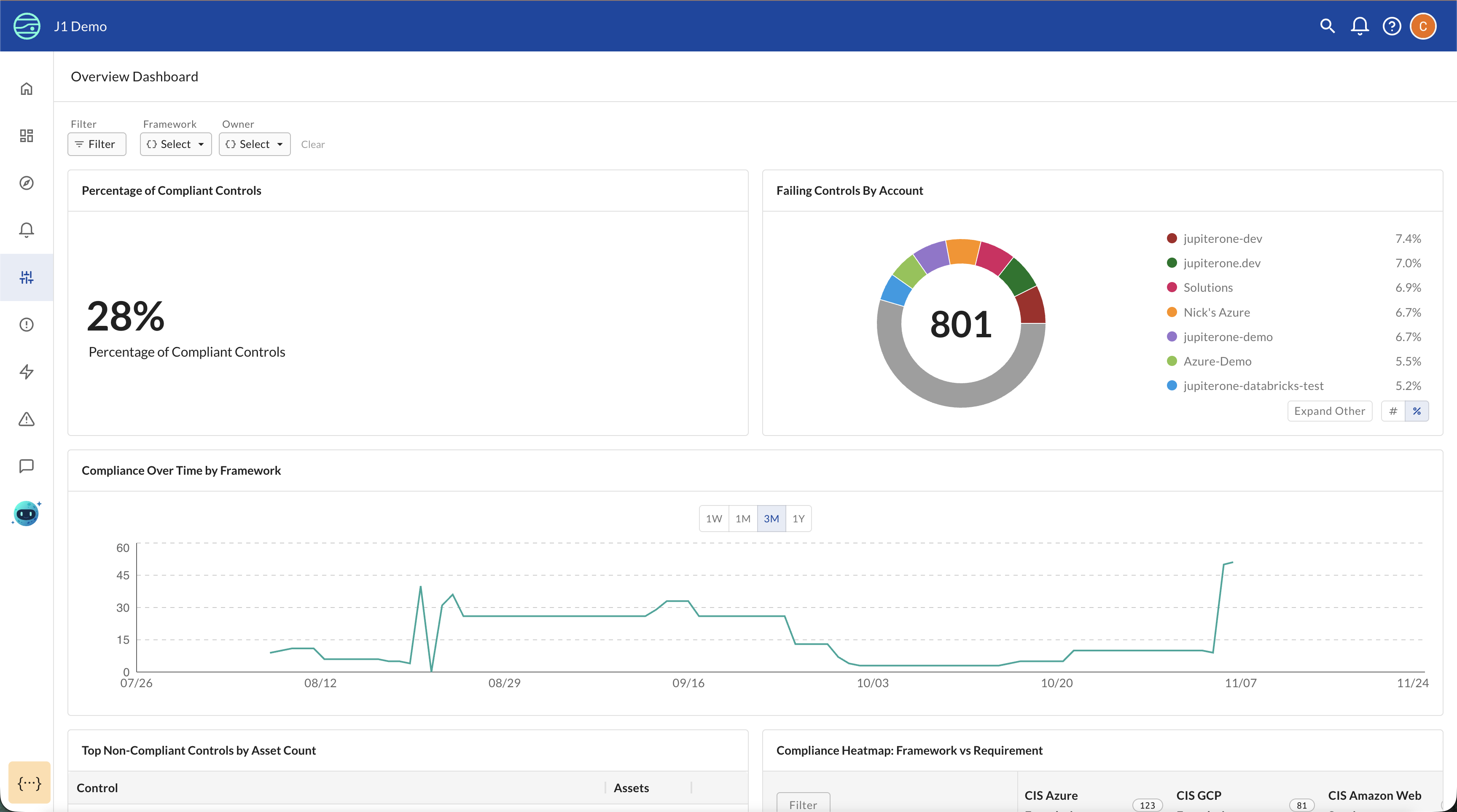
The CCM Overview Dashboard provides an at-a-glance view of your control monitoring status, showing:
- Total Controls: Complete count of all controls being monitored
- Compliant Controls: Number of controls with all tests passing
- Non-Compliant Controls: Number of controls with one or more tests failing
- Compliance trends over time: Historical view of how control compliance changes
- Failing controls by account: Breakdown of which cloud accounts or integrations have the most issues
JupiterOne's Unified Control Framework:
JupiterOne uses CIS Controls v8.0 as the unified control list for all out-of-the-box content. All mappings between different security standards (SOC 2, CIS standards, NIST etc.) and JupiterOne-managed controls follow the CIS v8.0 mapping framework. This provides a consistent, industry-standard foundation for cross-framework control reuse and ensures that a single control implementation can satisfy requirements across multiple compliance standards.
Data Model
CCM uses a four-level hierarchy to organize your compliance and security program:
Framework
└── Requirement
└── Control
└── Control Test
| Level | What it answers | Owned by | Example |
|---|---|---|---|
| Framework | What standards do we follow? | External standards body or your organization | CIS v8, SOC 2, HIPAA, or an internal security policy |
| Requirement | What must we achieve? | The framework | "Maintain an inventory of enterprise assets" |
| Control | How do we meet the requirement? | Your organization | "Automated asset discovery via JupiterOne integrations" |
| Control Test | Is our control actually working? | Your organization | J1QL query: FIND aws_iam_user WITH mfaEnabled != true |
A single control can satisfy multiple requirements across different frameworks, and each control can have multiple control tests for comprehensive validation.
Framework properties
| Property | Description |
|---|---|
| Title | Name of the framework |
| Description | Overview of the framework's purpose and scope (markdown) |
Requirement properties
| Property | Description |
|---|---|
| Title | Name of the requirement |
| Identifier | Reference code from the framework (for example, "CC6.1" or "IDAM3.5"). Used for sorting and filtering. |
| Priority | Criticality level: Critical, High, Medium, or Low |
| Description | What the requirement mandates (markdown) |
Control properties
| Property | Description |
|---|---|
| Title | Name of the control |
| Identifier | Reference code for the control. Used for sorting and filtering. |
| Catalog | Logical grouping for the control (for example, "CIS Controls v8"). You can select an existing catalog or create a new one. |
| Owner | The JupiterOne user responsible for the control |
| State | Lifecycle state: Draft, Review, Live, or Retired |
| Description | What the control does and why it matters (markdown, AI-assisted on create) |
| Remediation | Steps to take when the control is failing (markdown, AI-assisted on create) |
| Exception Process | How to handle approved exceptions (markdown) |
Control test properties
| Property | Description |
|---|---|
| Title | Name of the test |
| Type | Whether results represent Compliant assets or Non-compliant assets |
| J1QL | The query that runs against your JupiterOne asset graph |
View and Manage Modes
CCM has two modes that separate day-to-day monitoring from authoring workflows:
- View mode — Use this mode to review CCM results. You can browse frameworks, requirements, controls, and control test outcomes. This is the default mode for users who need to monitor compliance posture without making changes.
- Manage mode — Use this mode to author and edit frameworks, requirements, controls, and control tests. Switch to Manage mode when you need to create new content or modify existing definitions.
You can switch between modes using the toggle in the CCM navigation. View mode is read-only, so you cannot accidentally modify your control library while reviewing results.
View mode only displays Live controls and their results. Controls in Draft, Review, or Retired states are excluded from View mode counts and compliance metrics. Manage mode displays controls in all lifecycle states. This means framework control counts and compliance summaries will differ between the two modes.
How CCM Works
CCM's core capability is continuous, automated validation of control effectiveness using JupiterOne's query engine.
Automated Control Testing
How Control Tests Work:
- Each control has one or more test definitions
- Each test contains a J1QL query that runs against your asset graph
- Tests execute automatically on a regular schedule
- Control status updates based on whether all tests pass
Control Test Types
Each control test is either a Compliant assets test or a Non-compliant assets test. This determines how CCM interprets the query results.
| Test type | What it returns | How CCM interprets results |
|---|---|---|
| Compliant assets | Resources that satisfy the control | Results are expected — the more, the better |
| Non-compliant assets | Resources that violate the control | Any results indicate a problem |
Example Control Test:
A control for "Centralize Account Management" might have two tests:
- Test 1 (Non-compliant assets): Query for users WITHOUT SSO authentication — any results indicate a violation
- Test 2 (Compliant assets): Query for users WITH verified SSO — results confirm the control is working
Example Test Patterns:
- Non-compliant assets test: Find resources that violate the control
FIND aws_s3_bucket WITH encrypted = false - Compliant assets test: Verify required resources or configurations exist
FIND aws_cloudtrail WITH enabled = true
Key Features
Control Inventory and Management
CCM provides centralized monitoring of all your security and IT controls. The Controls list page displays:
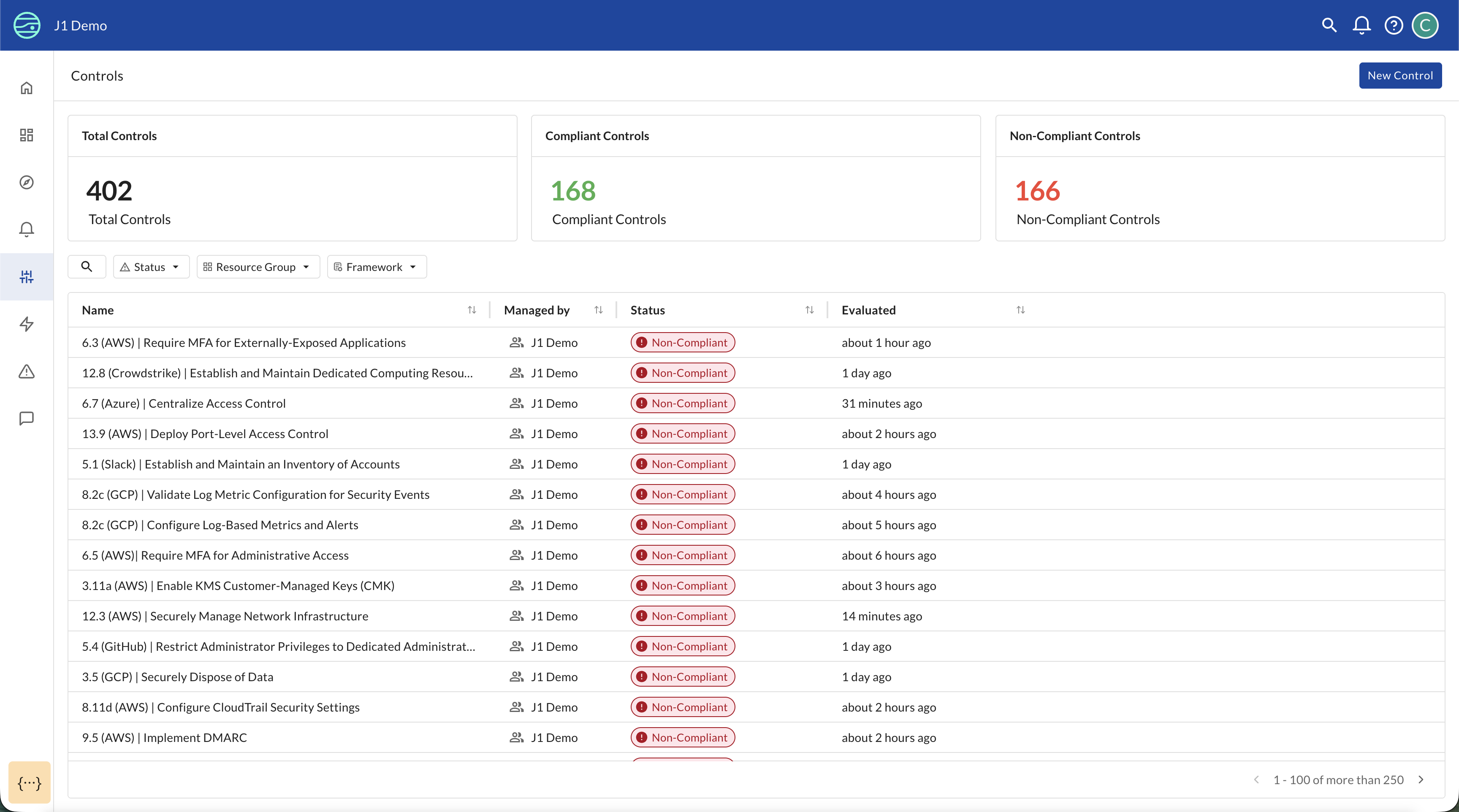
- Complete control inventory: Searchable and filterable list of all controls being monitored
- Real-time status: Current compliance state (Compliant/Non-Compliant/Not Configured) for each control
- Last evaluated timestamp: When each control was last tested
- Filtering options: Filter by status, lifecycle state, resource group, framework, or owner to focus on specific areas
Each control can be clicked to view detailed information including:
- Control tests: J1QL queries that validate whether the control is working
- Test results: Actual data showing what passed or failed
- Framework mappings: Which framework requirements this control satisfies
Viewing Control Test Results
When you click on a control, you can expand each test to see the J1QL query and actual results:
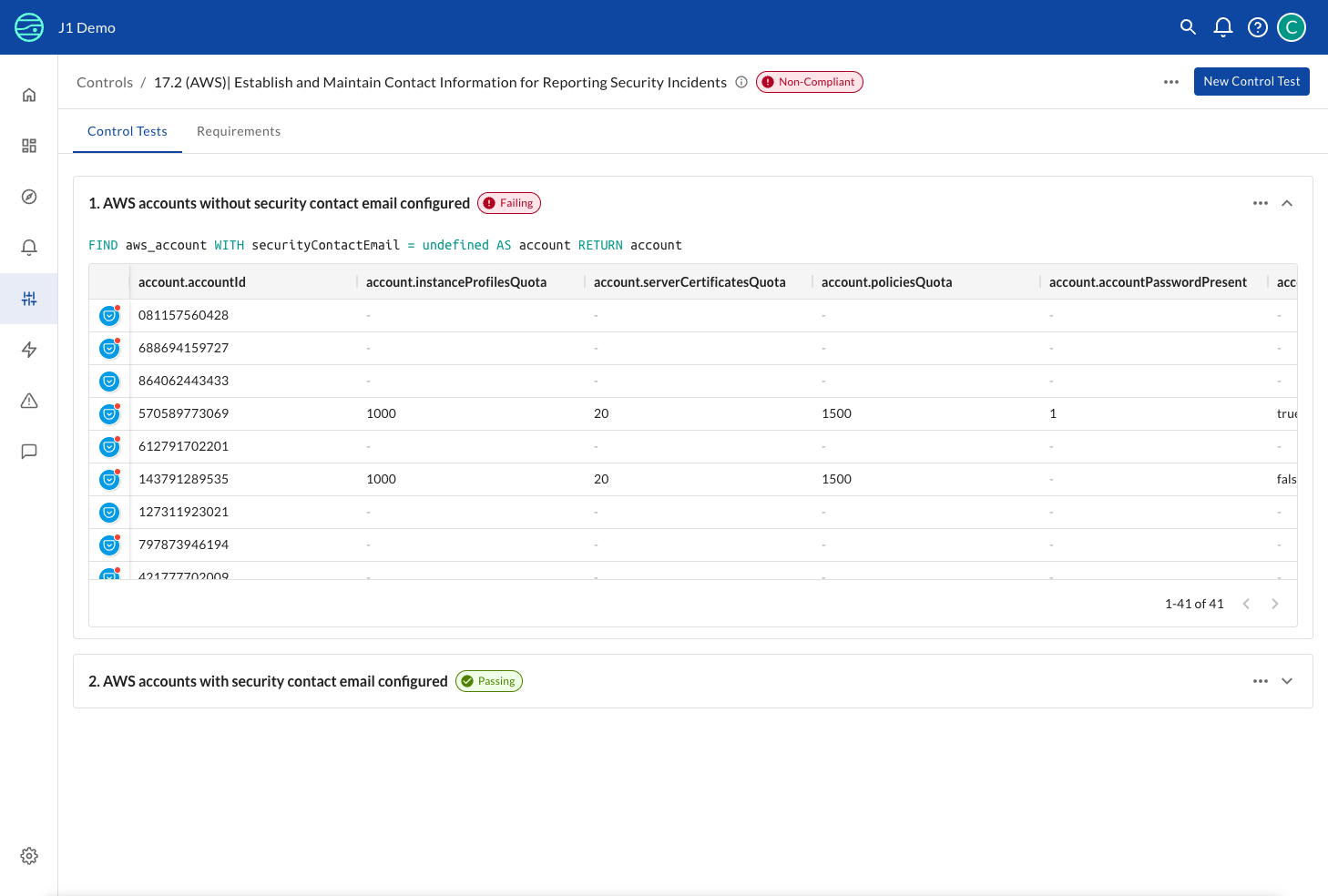
The control detail page shows:
- Control status: Overall status badge (Compliant/Non-Compliant)
- Test list: All tests defined for this control with individual pass/fail status
- J1QL queries: Click to expand any test to see the exact query being run
- Query results: Table view of actual assets that passed or failed the test
- Result count: Total number of resources affected (e.g., "1-41 of 41" accounts)
This detailed view enables you to:
- Investigate failures: See exactly which resources are violating the control
- Validate test logic: Review the J1QL query to ensure it's testing the right thing
- Collect evidence: Export query results for audit or remediation purposes
- Understand impact: Identify which accounts or resources need attention
Viewing Control Framework Mappings
Click the Requirements tab on any control detail page to see which framework requirements this control satisfies:
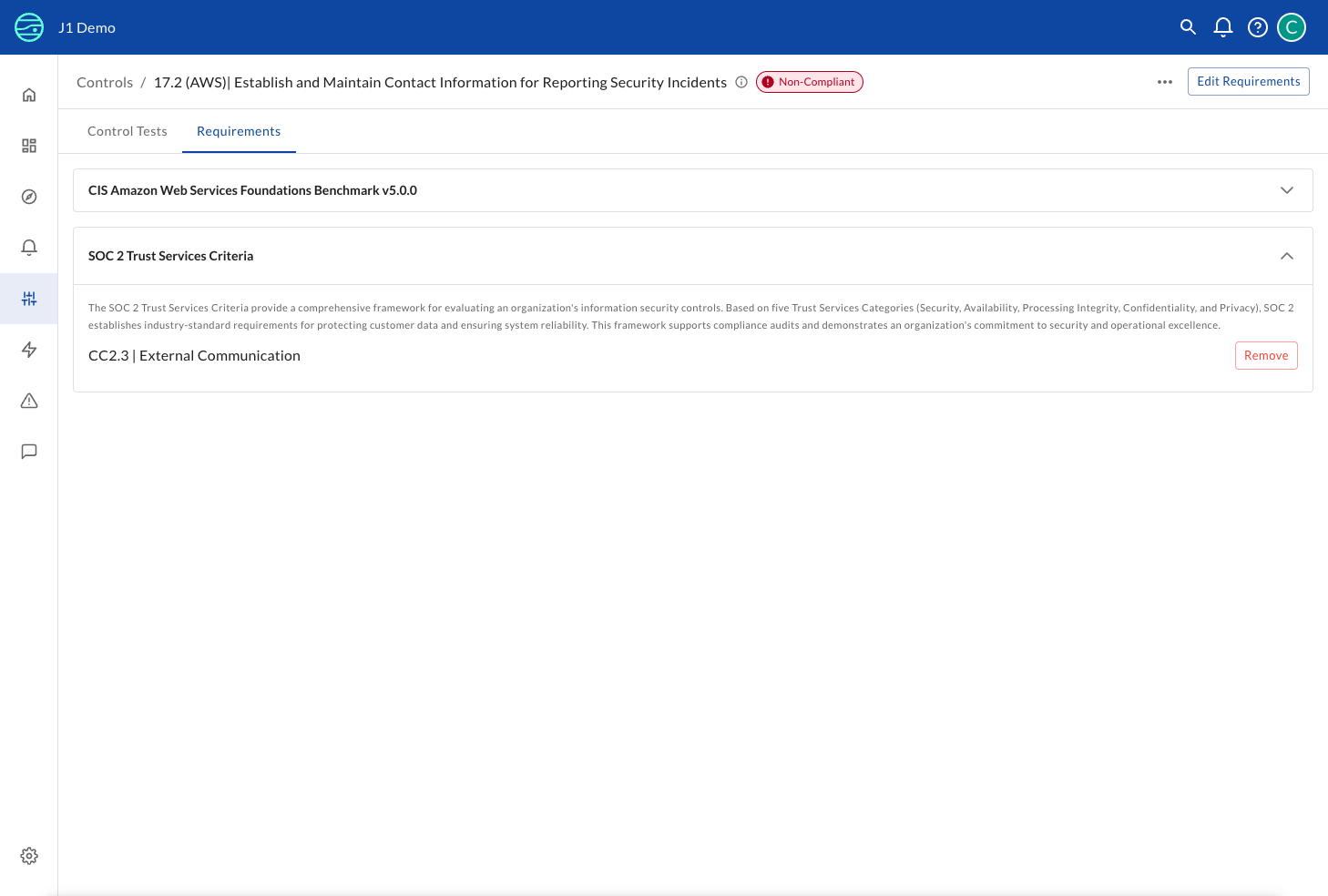
The Requirements tab shows:
- Framework name: Each framework the control maps to (e.g., "SOC 2 Trust Services Criteria", "CIS AWS Foundations Benchmark")
- Framework description: Brief overview of what the framework covers
- Specific requirement: The exact requirement within that framework (e.g., "CC6.1 | Logical and Physical Access Security")
- Edit Requirements button: Add or remove framework mappings for this control
- Remove buttons: Quickly unmap this control from a specific requirement
This view is useful for:
- Understanding control coverage: See which compliance requirements this control helps satisfy
- Managing mappings: Add this control to additional framework requirements or remove outdated mappings
- Cross-framework visibility: Identify controls that satisfy multiple standards simultaneously
- Audit preparation: Document which technical controls support each compliance requirement
Framework Management
Track control coverage across multiple security and compliance frameworks simultaneously:
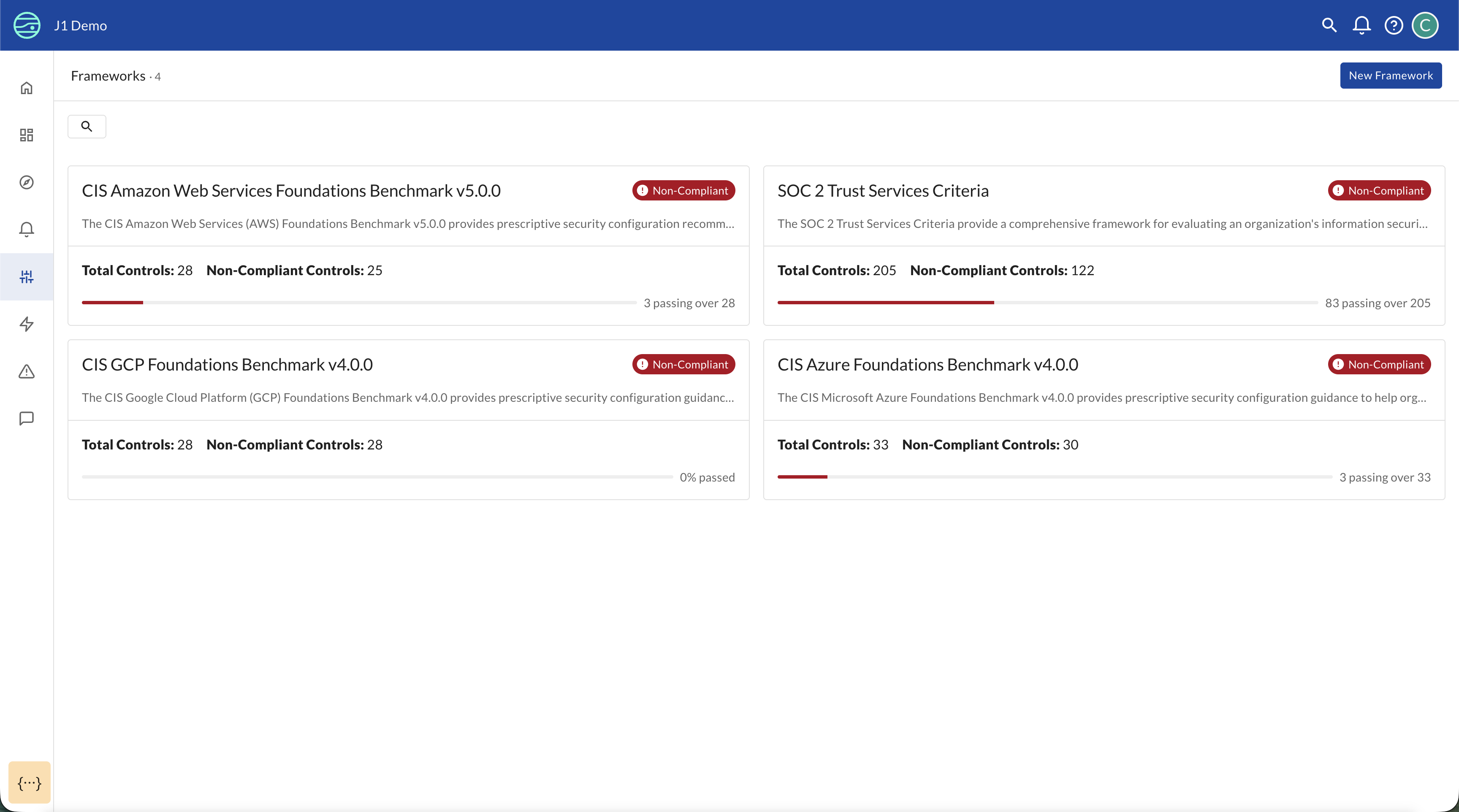
The Frameworks page shows:
- All available frameworks: JupiterOne provides out-of-the-box CIS benchmarks including AWS, Azure, GCP, Microsoft 365, GitHub, Oracle Cloud Infrastructure, and Kubernetes, with additional frameworks available based on customer demand
- Total controls per framework: How many controls are defined for each framework
- Passing controls: How many controls are currently passing out of the total (for example, "6 passing out of 51")
- Framework descriptions: Overview of what each framework covers
If you need a framework that is not listed, click Request a new Framework on the framework selection page to submit a request. JupiterOne will prioritize framework additions based on customer demand and configure controls relevant to your specific integrations.
Clicking into any framework provides detailed information about:
- Framework requirements and their hierarchical structure
- Which controls map to each requirement
- Control test status for that specific framework
- Gaps where requirements lack control coverage
Framework Details
Click on any framework from the Frameworks page to view comprehensive details:
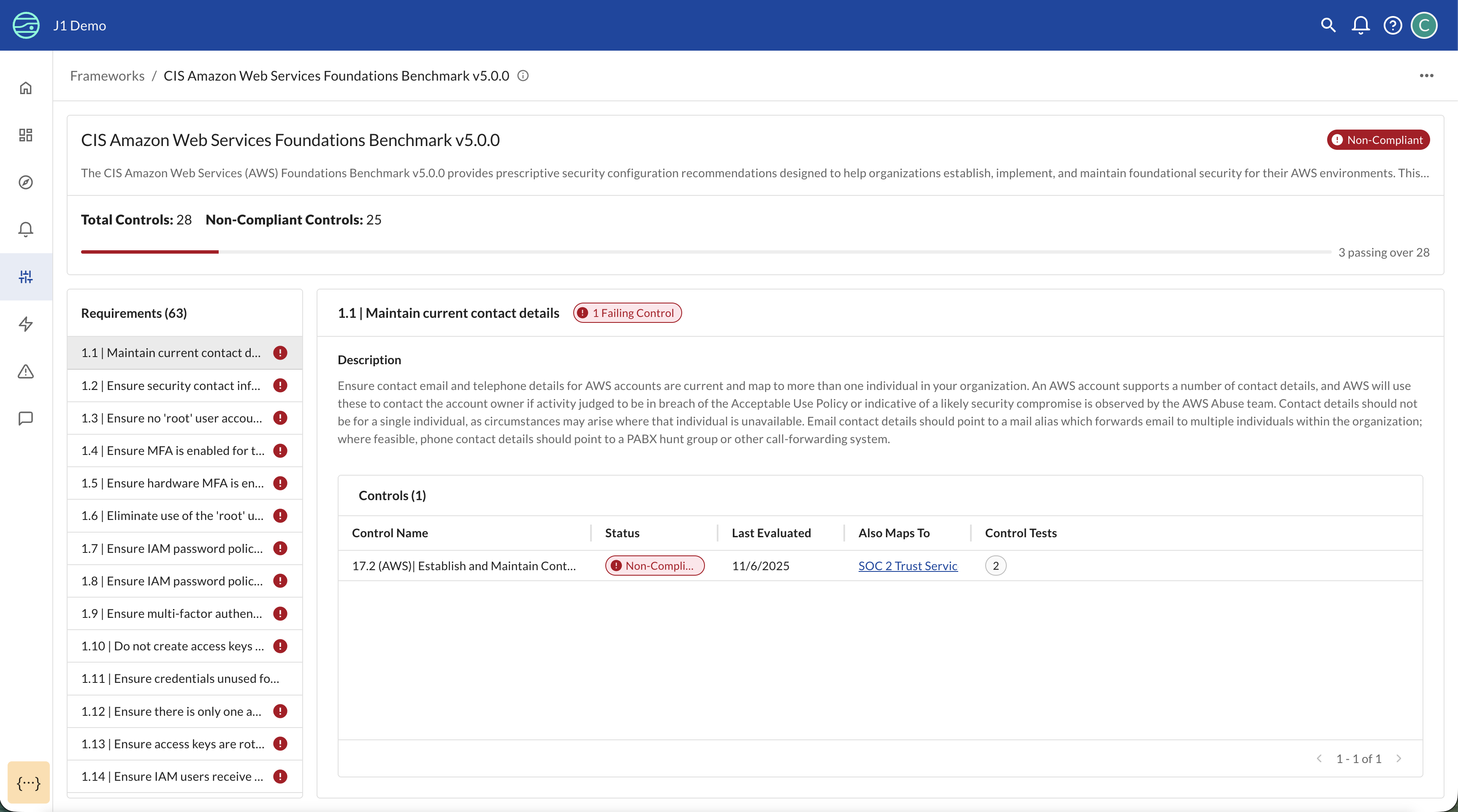
The framework detail page shows:
- Framework overview: Description and purpose of the framework
- Compliance metrics: Total controls, passing controls, and overall compliance percentage
- Requirements list: All requirements within the framework, organized hierarchically
- Control mappings: For each requirement, see which controls provide coverage
- Control status: Current pass/fail status for each mapped control
- Gap analysis: Quickly identify requirements that lack control coverage
Working with Frameworks
Understanding Control-to-Requirement Mapping
Controls in CCM can map to requirements across multiple frameworks. This allows you to:
- Reuse a single control definition across multiple compliance standards
- See which frameworks a control helps satisfy
- Understand the breadth of coverage provided by your control library
- Identify opportunities to consolidate duplicate controls
Creating and Managing Controls
Creating a New Control
To create a new control in CCM:
- Navigate to a framework requirement in Manage mode
- Click Add a control
- Define the control properties:
- Title: A clear, descriptive name for the control
- Identifier: A reference code for sorting and filtering (for example, "IAM-001")
- Catalog: A logical grouping (for example, "CIS Controls v8"). Select an existing catalog or create a new one.
- Description: What the control validates and why it matters (JupiterOne AI can generate this from the title)
- Remediation: Steps to take when the control is failing (JupiterOne AI can generate this)
- Exception Process: How to handle approved exceptions for this control
- Owner: The JupiterOne user responsible for maintaining and responding to this control
- Map the control to framework requirements
- Create control tests (J1QL queries) that validate the control
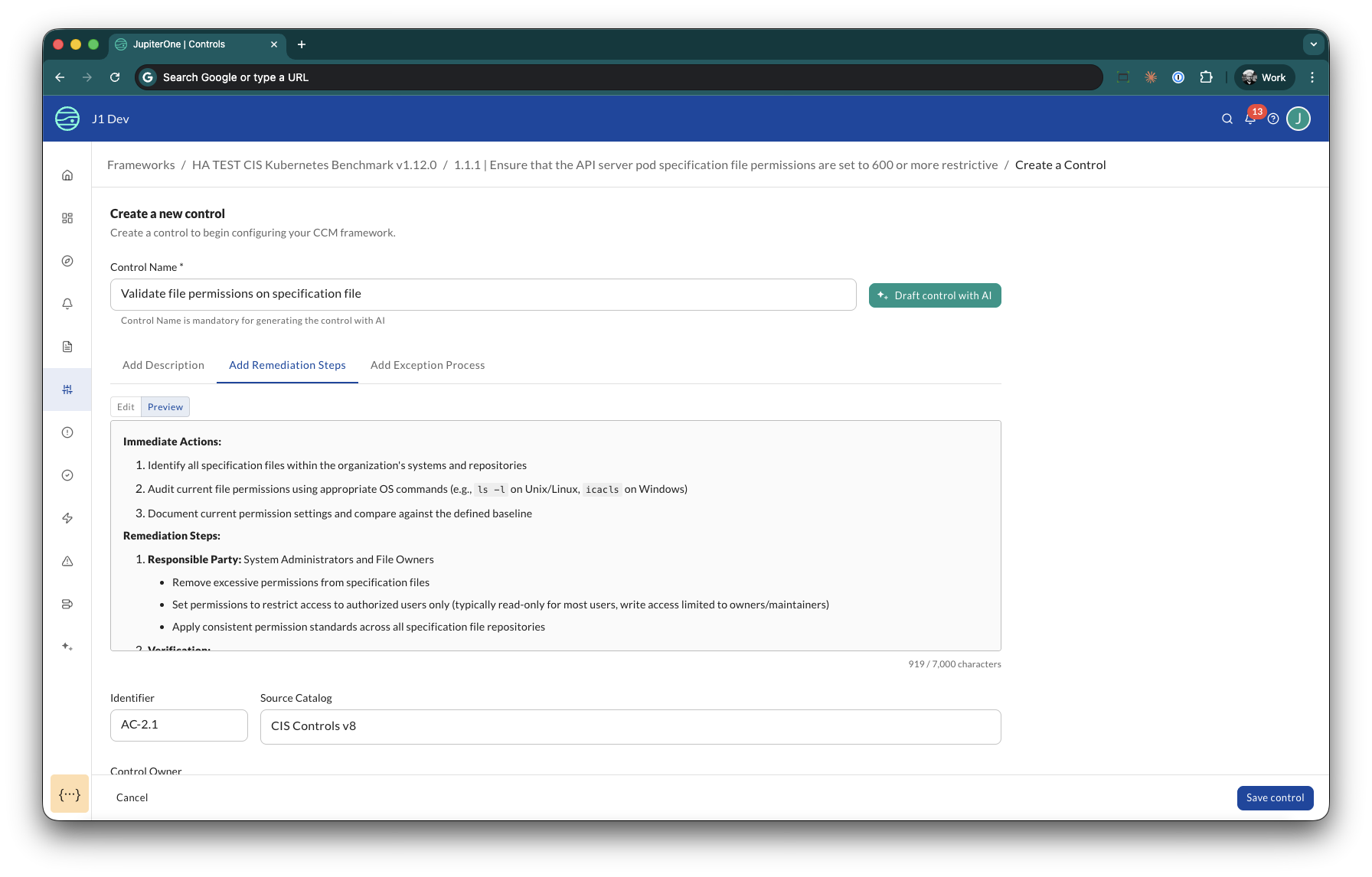
AI-Assisted Authoring
When you create a new control, JupiterOne AI can accelerate the process by generating content from your title:
- Enter a descriptive title for your control
- Click Draft control with AI — JupiterOne AI auto-generates the Description, Remediation steps, Identifier, and Source Catalog
- Review and edit any generated field — AI suggestions are not mandatory
JupiterOne AI uses context from the linked requirement to improve the quality of its suggestions.
AI-assisted generation is available when creating a new control. When editing an existing control, you update fields manually.
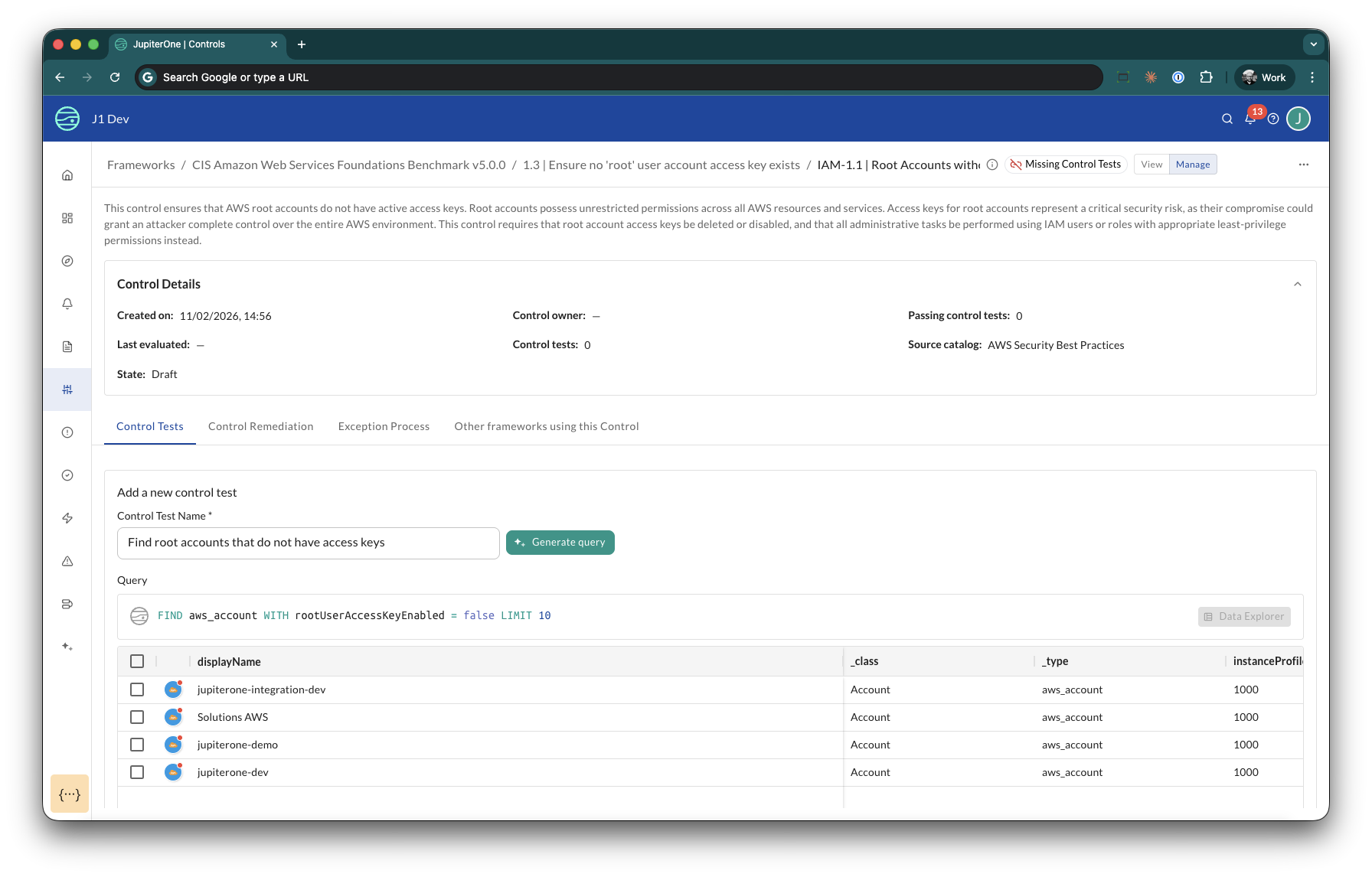
Creating Control Tests
Control tests are the core of CCM's automated validation. Each test:
- Contains a J1QL query that runs against your JupiterOne asset graph
- Defines expected outcomes — whether the results returned are Compliant assets or Non-compliant assets
- Runs automatically on a regular schedule
- Updates the control status based on whether expectations are met
AI-Assisted Test Creation
You do not need J1QL expertise to create control tests. JupiterOne AI can generate queries from a natural language description:
AI-assisted query generation is available when creating a new control test. When editing an existing test, you update the query manually.
- From a control, click New control test
- Enter a descriptive title for what you want to test
- Select the test type: Compliant assets or Non-compliant assets
- Click Generate query — JupiterOne AI generates a J1QL query based on your title and the control context, and automatically runs it so you can review matching entities
- Save the test
Mirror test creation: After you save a test, CCM prompts you to add the corresponding inverse test with the test type pre-selected. For example, if you save a Non-compliant assets test, it prompts you to create a Compliant assets test. This ensures comprehensive coverage with minimal effort.
Managing Existing Controls
From the Controls list, you can:
- Search and filter controls by status, framework, lifecycle state, or resource group
- View control details by clicking on any control
- Edit control tests to refine validation logic
- Update framework mappings to map controls to additional requirements
- Review test results to understand why a control is failing
- Assign an owner to establish accountability for each control
Control Catalogs
A catalog is a namespace for your controls. It groups controls by their origin or purpose, making it easier to organize and filter a large control library.
Examples of catalogs:
- "CIS Controls v8" — controls based on the CIS benchmark
- "Internal Security Policy" — controls defined by your organization
- "AWS Hardening" — controls specific to your AWS environment
When you create or edit a control, the Catalog field behaves like a tag selector. You can select an existing catalog or type a new name to create one. A control belongs to exactly one catalog.
Use catalogs to:
- Organize by source: Separate controls that come from different standards or internal teams
- Filter your library: Quickly find all controls within a specific catalog
- Manage at scale: When your control library grows beyond a few dozen controls, catalogs prevent the list from becoming unmanageable
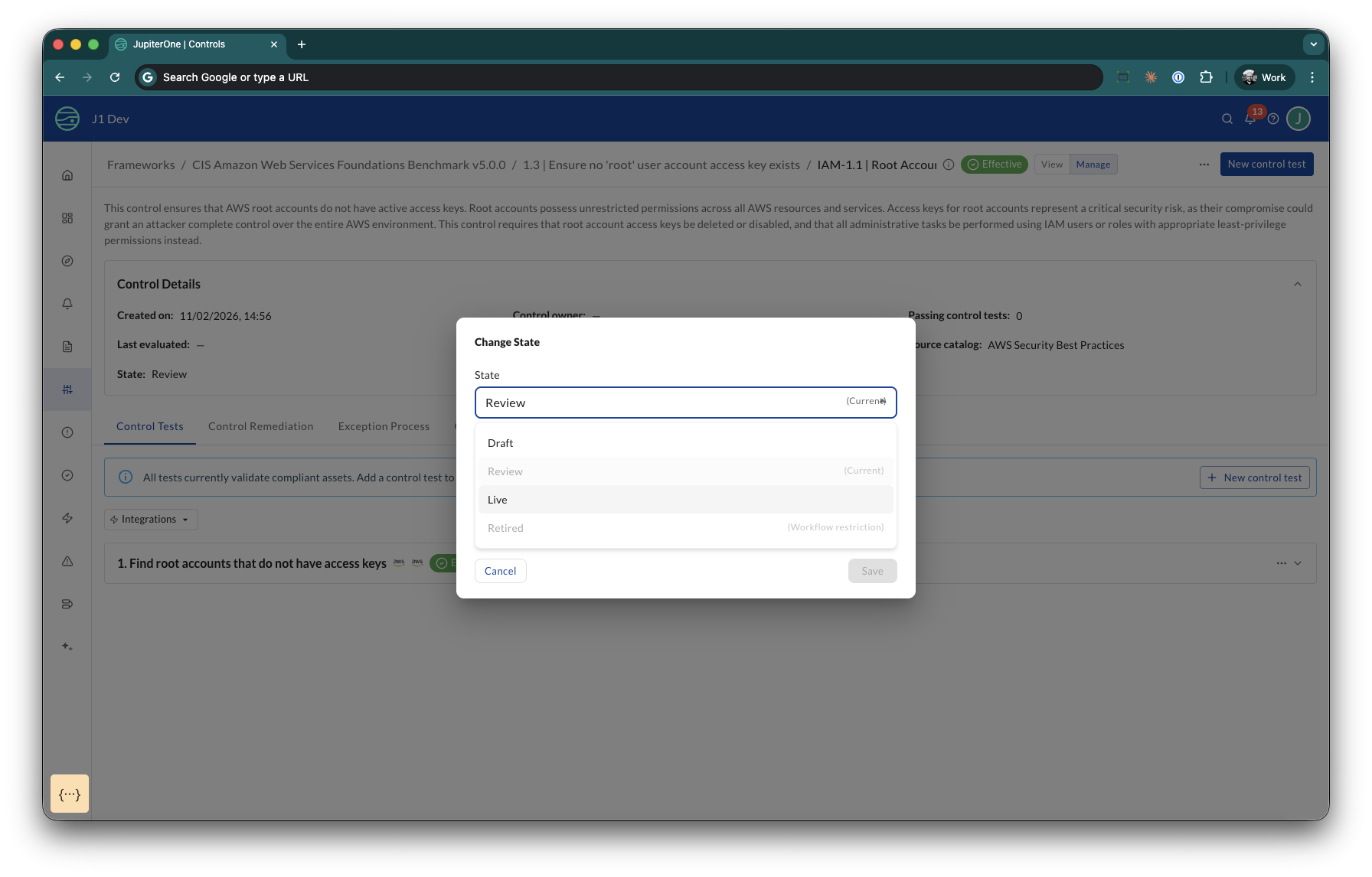
Control Lifecycle
Every control in CCM moves through a defined lifecycle that provides enterprise-grade governance for your control library.
Lifecycle states:
| State | Purpose |
|---|---|
| Draft | Control is being developed. This is the default state for new controls. |
| Review | Control is ready for validation by your team. |
| Live | Control is active and affects compliance scoring. |
| Retired | Control is no longer active but preserved for audit history. |
Key behaviors:
- Only Live controls are evaluated during compliance scoring
- Every state transition is recorded in an audit trail with optional notes
- You can filter your control library by lifecycle state
- Only Live controls count toward your entitlement limits
- Controls in Draft or Review allow you to develop and validate without affecting your compliance posture
To transition a control, click the lifecycle badge on the control detail page, select the target state, and optionally add a note explaining the reason for the transition.
Integration Awareness
CCM automatically detects which integrations a control test queries and provides real-time feedback on eligibility.
- When you author a control test, the UI shows which integrations provide data for your query
- If no matching entities exist for a test (for example, you have no AWS integrations but the test queries
aws_s3_bucket), the test shows No Datapoints - Tests with no datapoints are skipped during evaluation — they do not produce false failures
This prevents confusion when a test queries data from an integration you have not configured.
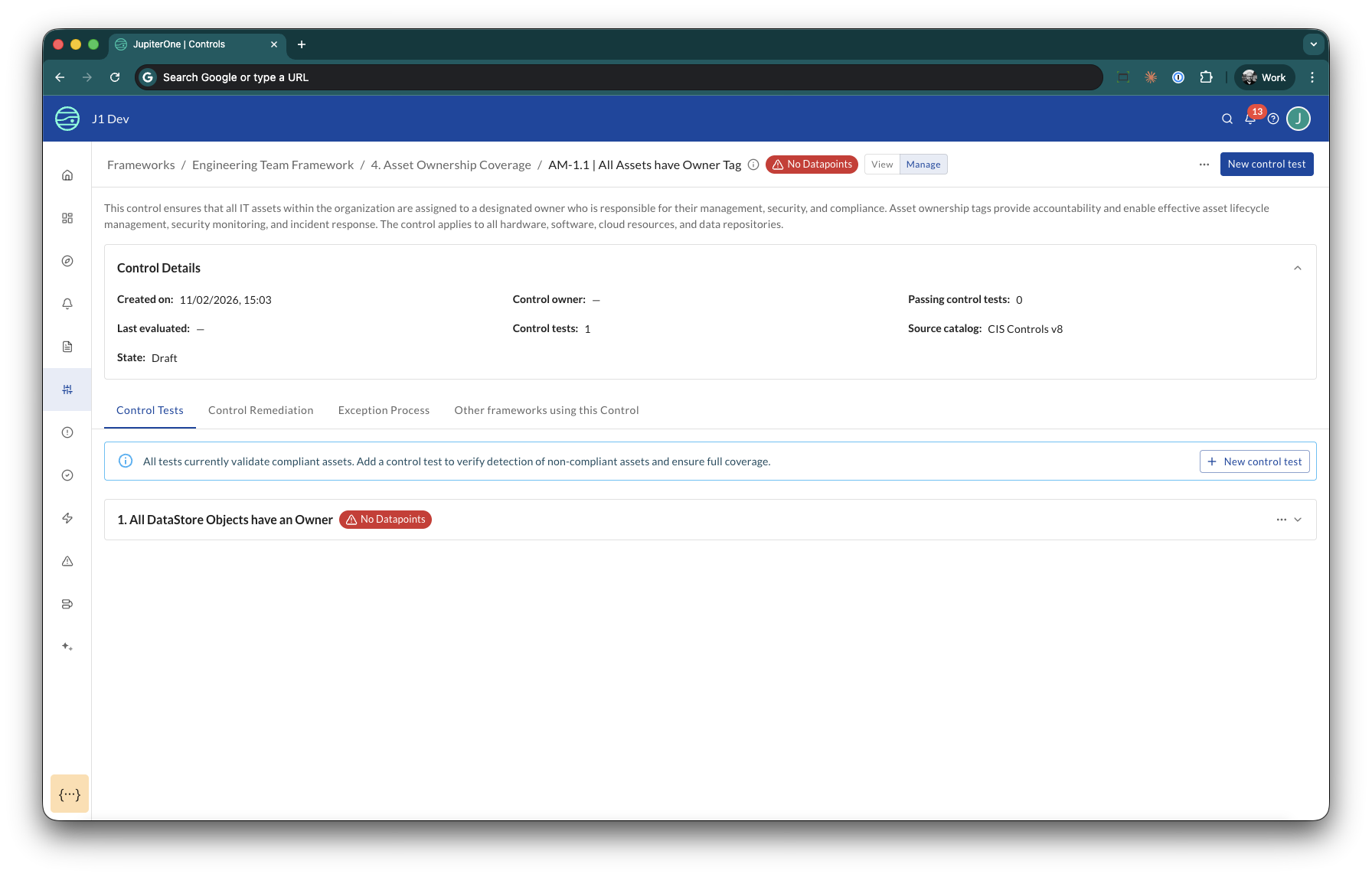
Control Effectiveness
CCM provides visual status indicators so you can instantly understand whether your controls are working.
Control test statuses:
- No Datapoints — The test query returned no matching entities. This replaces false failures when data is unavailable.
- Control tests that are effective (passing) are not decorated with a special status.
Control statuses:
- No Control Tests — The control has no tests configured.
- No Datapoints — All of the control's tests lack datapoints.
- Controls with at least one passing test that has datapoints show standard pass/fail results.
Status rolls up from the test level to the control level, and from the control level to the requirement level. You can see at every layer of your compliance hierarchy where attention is needed.
Getting Started
Step 1: Create or Import a Framework
- Switch to Manage mode using the toggle in the CCM navigation
- Navigate to Frameworks under the Controls tab in the nav bar
- Click Add a framework
- Choose one of the following options:
- Use Common Framework: Select an out-of-the-box CIS benchmark. If you need a framework that is not listed, click Request a new Framework to submit a request.
- Create your own Framework: Enter a title and description to build a custom framework directly
- Upload Your Own Framework (Beta): Import a PDF file
- Paste Framework JSON: Manually paste JSON configuration
- Select who has access to the framework by choosing a resource group. Resource groups control which users and groups can view and manage the framework. If you do not select a resource group, the framework is accessible to all users with CCM permissions.
- Add requirements to your framework, each with an identifier, priority, and description
Step 2: Understand Your Control Library
- From the Controls page, review the list of existing controls
- Click on a control to see:
- What it validates (control description)
- How it validates (J1QL queries in control tests)
- What frameworks it maps to (Requirements tab)
- Current test results
- Lifecycle state and effectiveness
Step 3: Create Your First Control
- From within a requirement, click Add a control
- Enter a title and click Draft control with AI — JupiterOne AI generates the description, remediation steps, identifier, and source catalog
- Review and edit the AI-generated content as needed
- Click New control test to add validation logic
- Describe what you want to test and click Generate query — JupiterOne AI generates and runs the J1QL query
- Review the results, then save
Step 4: Manage the Control Lifecycle
- New controls start in Draft state
- When the control is ready for review, transition it to Review
- After validation, move the control to Live to include it in compliance scoring
- Add notes at each transition for your audit trail
Step 5: Map Controls to Framework Requirements
- From a control detail page, click the Requirements tab
- Click Edit Requirements to add framework mappings
- Select the framework and specific requirement(s) this control satisfies
- Save your mappings
Step 6: Monitor and Refine
- Return to the Overview Dashboard regularly to track control health
- Switch to View mode to review control status and identify controls that need attention
- Investigate non-compliant controls to understand root causes
- Refine control test queries based on false positives or misses
- Expand your control library to cover additional requirements
Best Practices
To maximize the value of Continuous Control Monitoring:
Start with Your Governance Framework
- Begin with controls that are already defined in your IRM or governance system
- Map those controls to framework requirements in CCM
- Use CCM to automate the evidence collection and validation for those controls
Design Effective Control Tests
- Write specific queries: Focus on precise validation criteria rather than broad checks
- Use negative tests: Often easier to detect violations (what shouldn't exist) than prove compliance
- Combine multiple tests: Use both positive and negative tests for comprehensive coverage
- Test your queries first: Run J1QL queries manually in the Query Builder before adding them as control tests
- Handle exceptions: Consider using tags or properties to exclude known exceptions from test results
Organize Controls Strategically
- Group by technology domain: Separate controls for AWS, Azure, GCP, SaaS applications
- Map to multiple frameworks: Reuse controls across frameworks where applicable
- Use consistent naming: Follow a naming convention for easier management (e.g., "5.6 (AWS) | Control Name")
- Document control intent: Write clear descriptions explaining what the control validates and why
Integrate with Your Workflow
- Connect to your IRM: Use JupiterOne's API to feed control status back to ServiceNow, Archer, or other governance platforms
- Set up alerts: Configure alerts for critical control failures that need immediate attention
- Schedule reviews: Regularly review control test results with your security and platform teams
- Track trends: Monitor control compliance over time to identify systemic issues
Scale Gradually
- Start with 10-20 critical controls for your most important framework
- Validate that tests are accurate and provide meaningful results
- Expand coverage to additional frameworks and control areas
- Refine test logic based on false positives or missed violations