JupiterOne August 2023 Release
We have officially migrated our documentation to our new site here at docs.jupiterone.io! 🥳
New Features and Improvements
Queries
Natural Language Queries
JupiterOne now supports natural language to generate J1QL (JupiterOne query language). You can now type questions like "What new IAM users have been created in the last week?" and "What s3 buckets do I have?" and J1 will convert these questions into J1QL syntax. This feature is currently only available in the Query Anywhere Search Box

Improvements
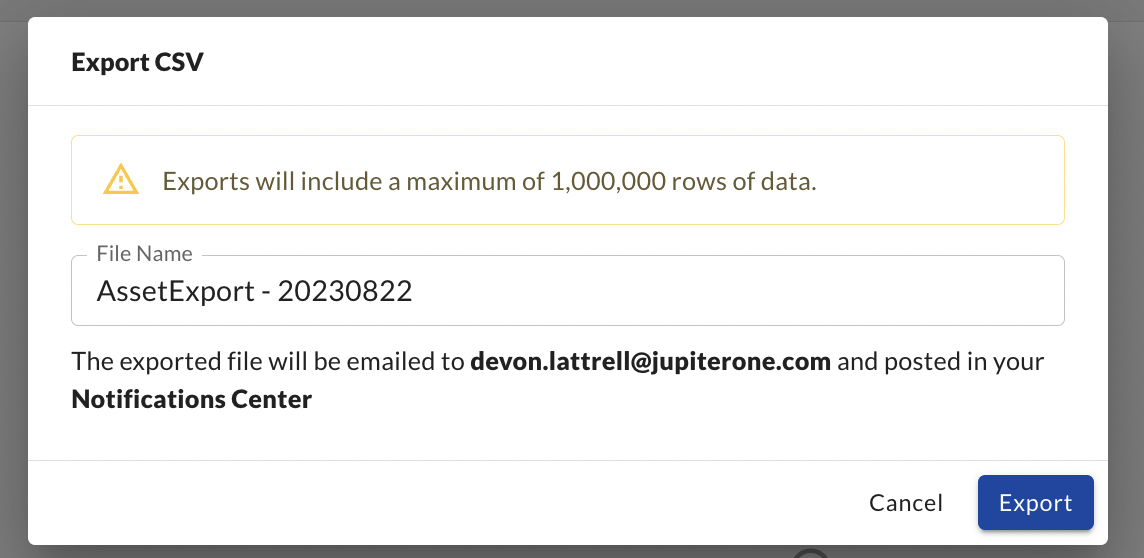
The csv exporting experience has been upgraded to allow for larger downloads (1 million entity limit) and an email link to access your downloaded file.
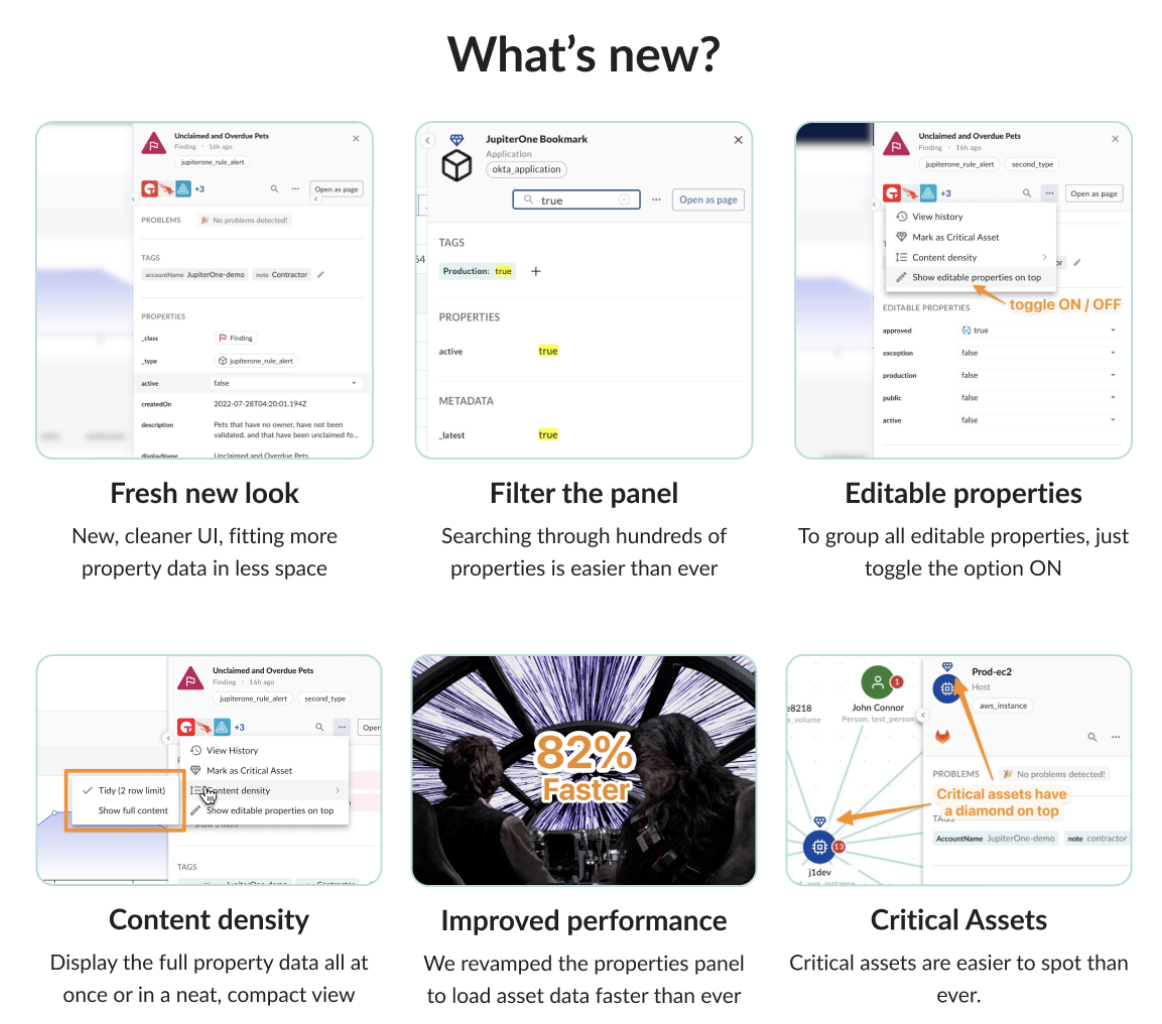
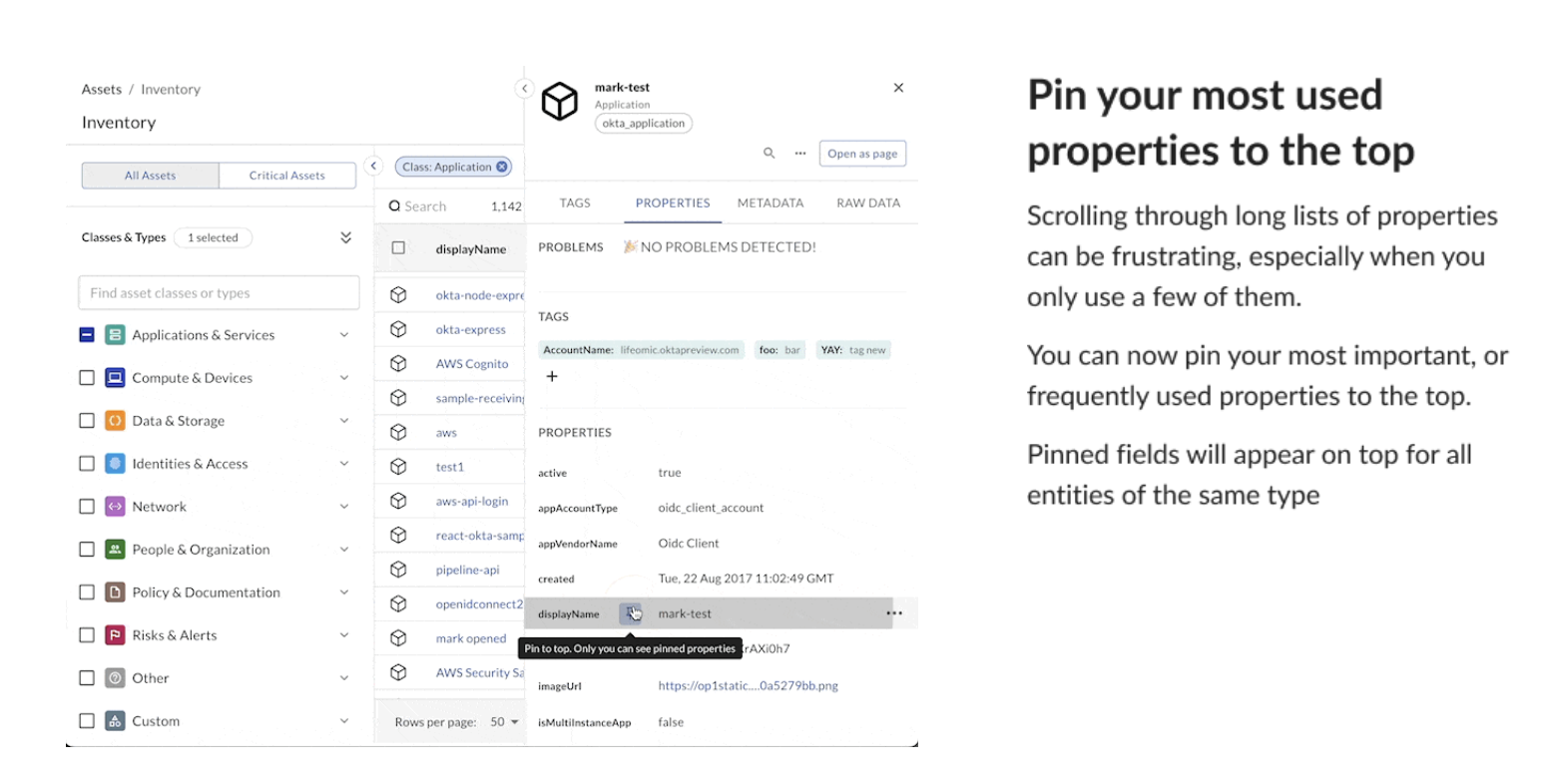
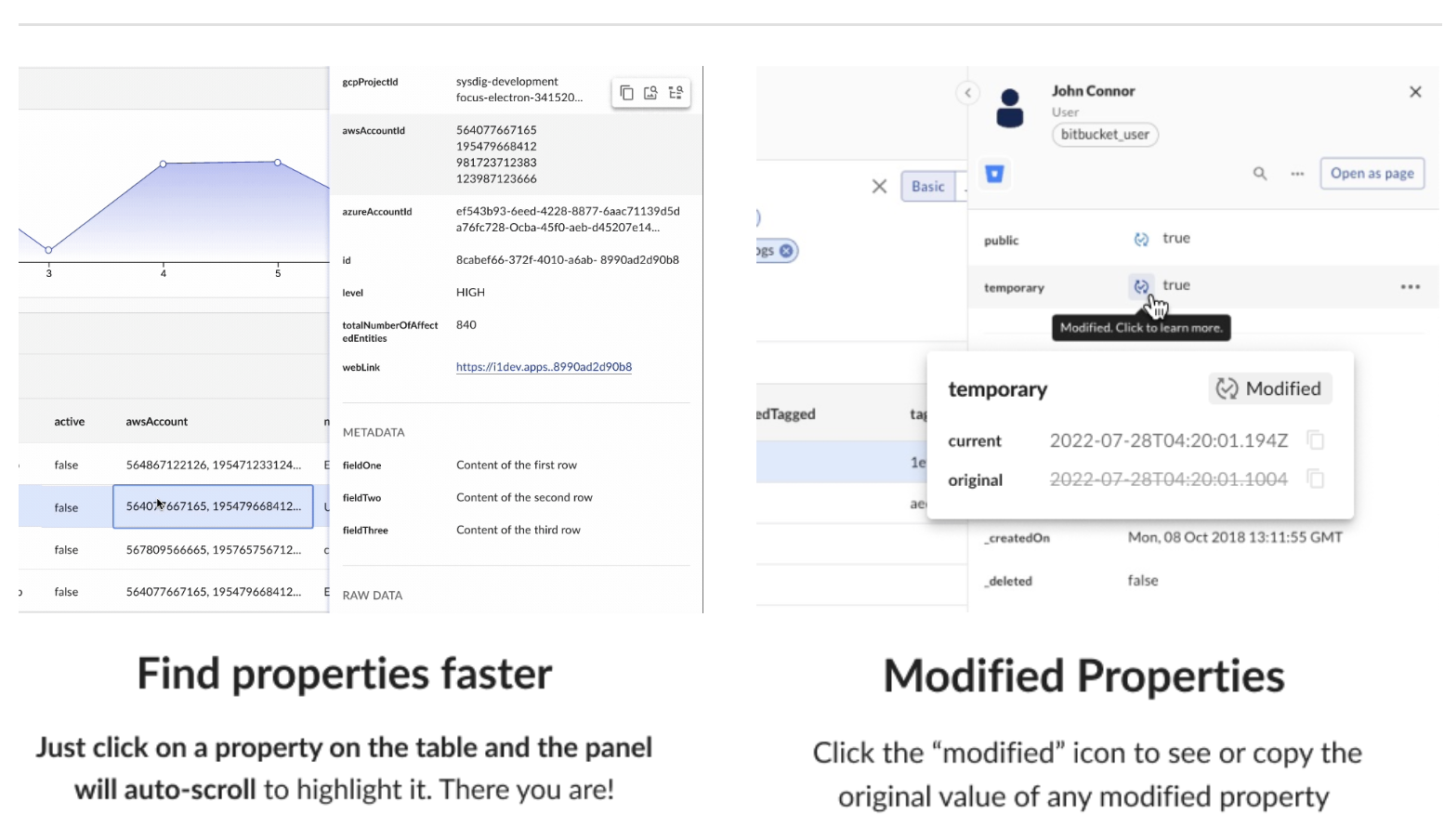
Properties Panel
Your Properties Panel has been refreshed with a whole new look and new features to help you find what you are looking for faster in JupiterOne.
Insights
- Added two new Insights dashboards corresponding to our new Alert Rule Packs for
Device ManagementandToxic Combinations.- The
Device Managementdashboard can be found under Assets and requires at least one integration that ingests devices - The
Toxic Combinationsdashboard can be found under Attack Surface category and requires integration into J1 of your Endpoint Detection & Response tools, Mobile Device Management, Cloud Service Provider, and Identity Provider systems
- The
Alerts and Rules
-
Released two new Alert Rule Packs: Device Management and Toxic Combinations, both of which are tagged in Alerts as
DeviceManagementandToxicCombinationsrespectively. -
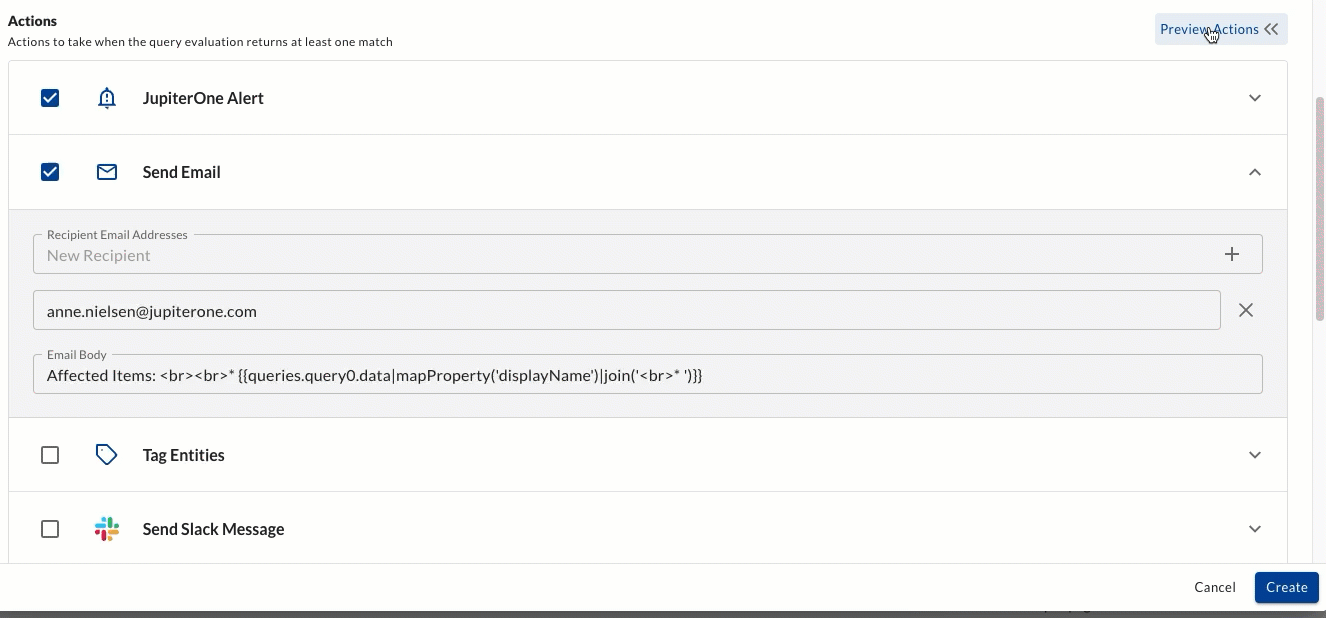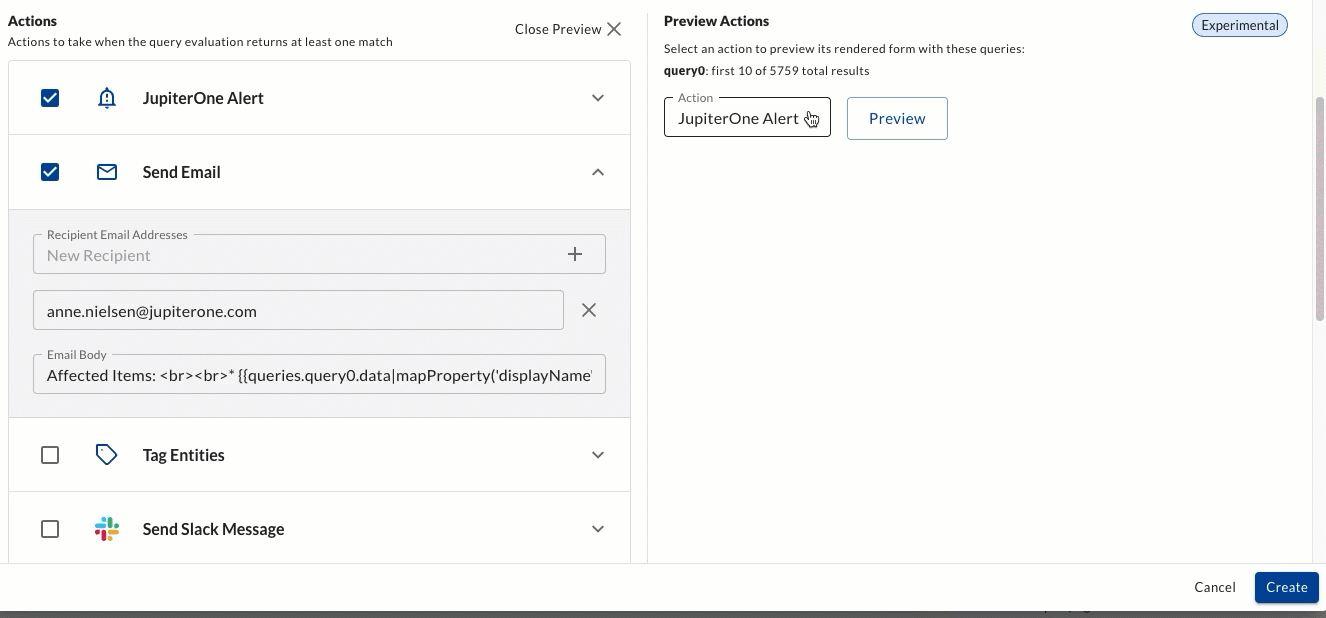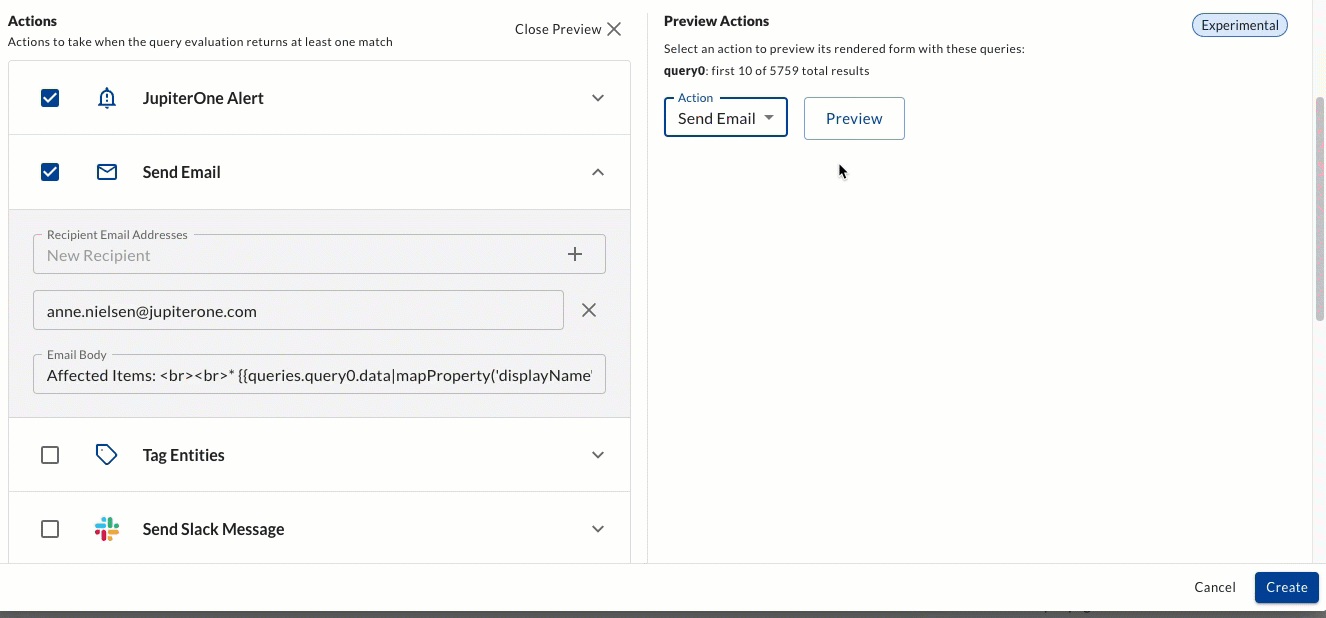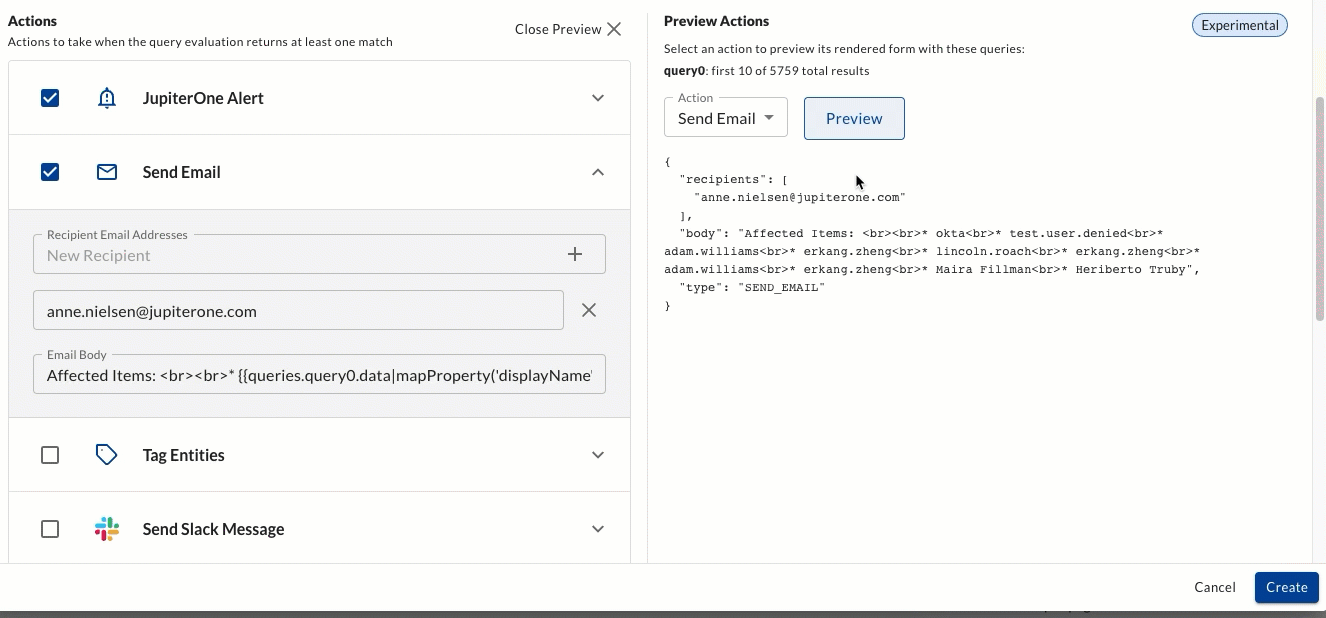
You can now preview your Alert Rule Action using the "preview" toggle. This allows you to see the json for the first 10 query results which power your alert.
Integrations
New Integrations
-
Linear (beta): Added integration for Linear Read more →
-
FleetDM (beta): Added integration for FleetDM Read more →
Updates
-
AWS: In the US environment of JupiterOne (apps.us.jupiterone.io), the
Trust Relationshipon the AWS IAM Role used by the AWS Integration has been changed to trust 5 additional JupiterOne-owned AWS accounts. In addition to the original JupiterOne AWS Account ID (612791702201), the role should be updated to trust the following 5 AWS Account IDs: -
592277296164 -
543056157939 -
688694159727 -
248422699954 -
703115985002
The public GitHub repository for CloudFormation & Terraform templates has been updated accordingly. This is change helps to reduce AWS rate limits and is highly encouraged, but not required–all AWS integrations will continue to function as expected without these changes. Please reach out to your account representatives with additional questions.
- Azure: Added the ability to ingest MFA properties for the
azure_userentity. New properties include:mfaEnabled(boolean)mfaType(string, the user preferred method)mfaMethods(array of strings, includes all MFA methods the user has configured)
Your Azure instance API token will need to have the AuditLog.Read.All permission in order to ingest the MFA properties.
-
CrowdStrike: Our CrowdStrike integration now ingests information on applications with vulnerabilities with the following new entity:
Resource Entity _typeEntity _classApplication crowdstrike_applicationApplicationWith the addition of this entity, we have also updated the relationships:
Source Entity _type | Relationship _class | Target Entity _type |
|---|---|---|
crowdstrike_account | HAS | crowdstrike_endpoint_protection |
crowdstrike_account | HAS | crowdstrike_sensor |
crowdstrike_application | HAS | crowdstrike_vulnerability |
crowdstrike_prevention_policy | ENFORCES | crowdstrike_endpoint_protection |
crowdstrike_sensor | ASSIGNED | crowdstrike_prevention_policy |
crowdstrike_sensor | HAS | crowdstrike_application |
crowdstrike_sensor | HAS | crowdstrike_zero_trust_assessment |
crowdstrike_vulnerability | EXPLOITS | crowdstrike_sensor |