Armis
The Armis integration adds comprehensive device visibility and threat detection capabilities. This integration enables JupiterOne users to better manage assets, assess risks, and respond to incidents more effectively by leveraging Armis's device insights.
- Installation
- Data Model
- Types
Installation
To install this integration, you will need to configure settings both within Armis and on JupiterOne. Before enabling in JupiterOne, ensure that you complete the setup within your Armis's account.
Configuration on Armis
You will have to configure an API secret key in Armis so that the integration can make REST API calls to fetch data from Armis.
-
Using a web browser, go to your Armis tenant (e.g.
https://my-tenant.armis.com) and log in with your credentials. -
Click on Settings -> API Management
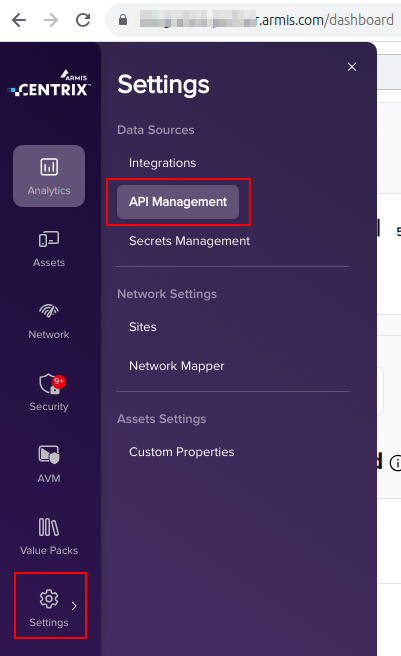
-
Click on the
Createbutton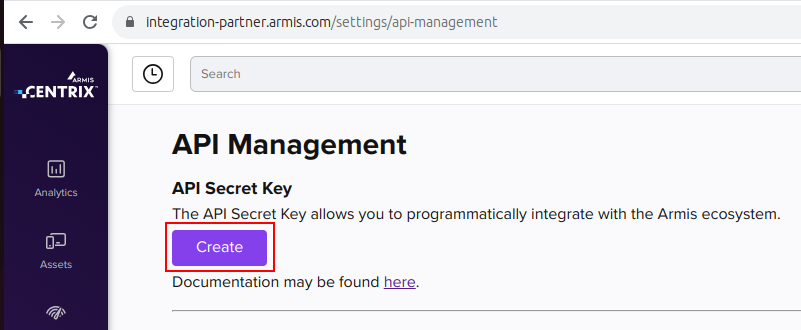
-
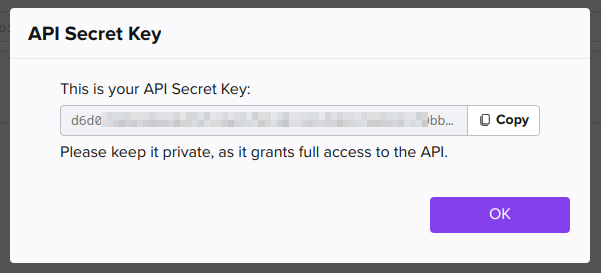
You will get a message box with the newly created API Secret Key. Save the key in a safe place, you will need this to configure the integration in JupiterOne.
Data Volume Configuration
Control how much data is ingested from Armis to manage storage and processing.
Ingestion Windows (Time Ranges)
| Field | Description | Default | Options |
|---|---|---|---|
| Historical Days | Number of days for which data should be retrieved from Armis | 90 | Any number greater than 0 |
| Vulnerabilities Ingestion Window | Ingestion window for vulnerabilities last detected (days ago) | 90 | 90, 180, 275, 365 |
How it affects data volume: Higher number of days will result in more devices, alerts, and vulnerabilities being ingested from Armis.
Data Filtering Options
| Field | Type | Description | Default |
|---|---|---|---|
| Included Vulnerability Severities | Multi-select | Select vulnerability severities to ingest | Critical, High, Medium |
| Included Vulnerability Status | Multi-select | Select vulnerability status to ingest | Open |
How it affects data volume: Filtering by severity and status reduces the number of vulnerability entities ingested. By default, only Critical, High, and Medium severity vulnerabilities with Open status are imported.
Finalize in JupiterOne
To install the Armis integration in JupiterOne, navigate to the Integrations
tab in JupiterOne and select Armis. Click New Instance to begin configuring
the integration.
Creating an integration instance requires the following:
-
Enter the Armis URL (e.g.
https://<tenant>.armis.com) -
Enter the Armis API Secret Key generated for use by JupiterOne.
-
Enter the account name by which you want to identify this Armis account in JupiterOne.
-
[Optional] Enter a description to help your team identify the integration.
-
[Optional] Select a polling interval that is sufficient for your monitoring requirements. You can leave this as
DISABLEDand manually execute the integration. -
[Optional] Enter the Historical Days (any number greater than 0). The integration will ask Armis to return devices/alerts seen in the last few days. The Historical Days number will be used for this query. Higher number of days will result in more data ingested.
-
[Optional] Disable TLS Verification - Set this to true only if you have an on-prem Armis server that does not have a valid SSL certificate configured. For most cases this value should be false.
Click Create once all values are provided to finalize the integration.
Next steps
Now that your integration instance has been configured, it will begin running on the polling interval you provided, populating data within JupiterOne. Continue on to our Instance management guide to learn more about working with and editing integration instances.
Entities
The following entities are created:
| Resources | Entity _type | Entity _class |
|---|---|---|
| Account | armis_account | Account |
| Alert | armis_finding_alert | Finding |
| Device | armis_device | Host |
| Site | armis_site | Site |
| Vendor | armis | Vendor |
| Vulnerability | armis_finding_vulnerability | Finding, Vulnerability |
| Vulnerability | armis_finding_vulnerability | Finding |
Relationships
The following relationships are created:
Source Entity _type | Relationship _class | Target Entity _type |
|---|---|---|
armis | HOSTS | armis_account |
armis_account | MANAGES | armis_device |
armis_account | HAS | armis_site |
armis_device | HAS | armis_finding_vulnerability |
armis_device | HAS | armis_finding_alert |
armis_site | HAS | armis_device |
Armis Device
armis_device inherits from Host
| Property | Type | Description | Specifications |
|---|---|---|---|
_key * | string | ||
ipAddress | string | ||
ipv6 | string | ||
macAddress | string |
Armis Finding Vulnerability
armis_finding_vulnerability inherits from Finding, Vulnerability
| Property | Type | Description | Specifications |
|---|---|---|---|
blocking * | boolean | null | ||
production * | boolean | null | ||
public * | boolean | null | ||
remediationActions * | string | null |
Armis Finding Vulnerability
armis_finding_vulnerability inherits from Finding
| Property | Type | Description | Specifications |
|---|---|---|---|
blocking * | boolean | null | ||
production * | boolean | null | ||
public * | boolean | null | ||
remediationActions * | string | null |